Nmap Output Formatting
This post concentrates on assembling and presenting various types of outputs that Nmap provides. Sometimes, Nmap output is difficult to read, especially when scanning large networks with large amount of hosts. Nmap output options ensure, that the output is easily interpreted, organised and readable by different penetration testers working on the same project. The output formats also ensure that the output can be utilised in harmony with other required pieces of software, such as Metasploit. The output examples presented in this post are a result of a private network scan. This post does not explain the utilisation of various Nmap scan options as that’s beyond the scope of this post.
Normal Output (-oN)
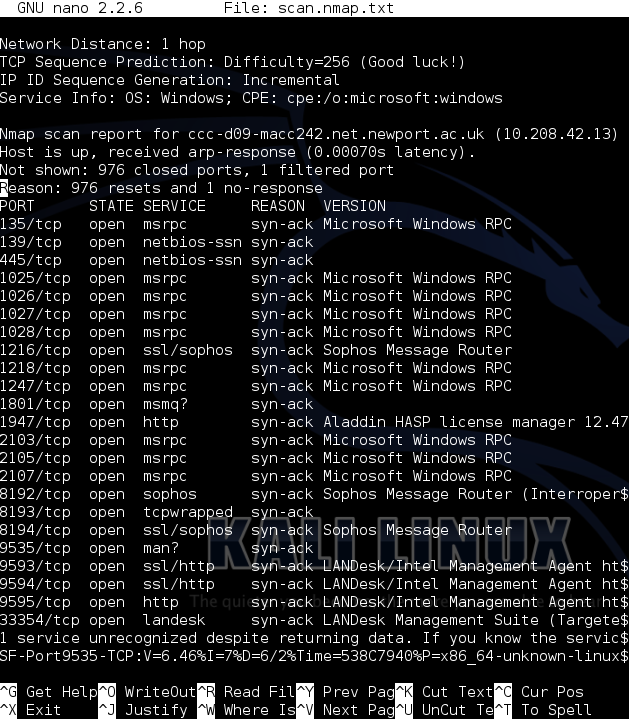
Normal output is very similar to output that Nmap provides without writing any formatting commands, however adding -oN option enables the opportunity to output the standard output into a specified text file and also strips down information that are relevant only during the scan, such as “Discovered open port 80/tcp on 10.208.42.40” or “Initiating SYN Stealth Scan at 14:52”. Such messages are only outputted in verbose modes -v and -vv.
The Command Utilised
nmap -O -v -sV --reason --open -oN scan.nmap.txt 10.208.42.0/24
-oN—initiates Normal Output mode
scan.nmap.txt—specifies the file for the scan output to be saved
Normal Output in Nano
For this particular network, the text file contains 424 lines of information, which could create problems if you want to find a particular host. Normal output is suitable for single hosts or very small networks.
Grepable Output (-oG)
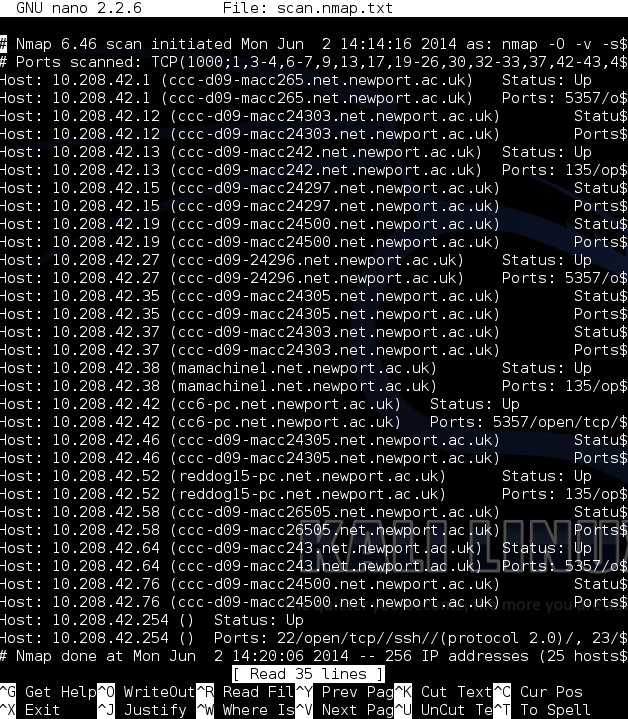
Greapable output formats the standard text output to be easily utilised by other Linux/Unix tools such as grep awk cut or diff. Each scanned host, its port and OS information is listed in a new line separated by the tab, slash and comma characters which define boundaries for such commands.
The Command Utilised
nmap -O -v -sV --reason --open -oG scan.nmap.txt 10.208.42.0/24
-oG—initiates Grepable Output mode
scan.nmap.txt—specifies the file for the scan output to be saved
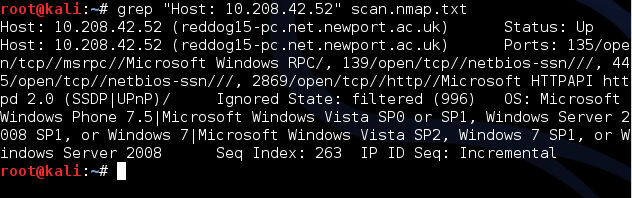
Greapable Output in Nano
grep "Host: 10.208.42.52" scan.nmap.txt —displays all the information about the host 10.208.42.52 from the grepable output.
There are more commands that are able to process information from the Greapable Output more clearly and precisely, however that’s beyond the scope of this post.
XML Output (-oX)
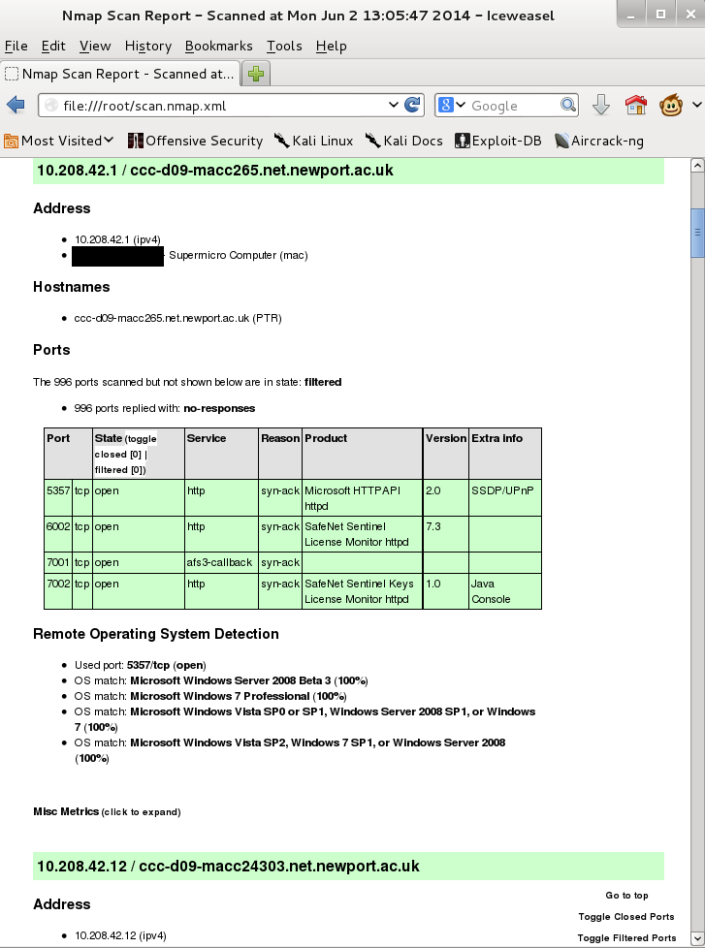
XML Output is my favourite output option as it is the most flexible. XML files can be opened in web browsers and also implement in Metasploit to populate workgroups very easily. XML output requires Extensible Stylesheet Language (XSL) file to be specified in order to transform and render XML into HTML. In Kali, a XSL stylesheet is provided in Nmap directory /usr/share/nmap/nmap.xsl. If the entire path is specified in the Nmap command, the conversion does not work. The conversion works only if nmap.xsl resides within /root/ directory.
The Command Utilised
nmap -O -sV --reason --open -oX scan.nmap.xml --stylesheet=nmap.xsl 10.208.42.0/24
-oX—initiates XML Output mode
scan.nmap.txt—specifies the file for the scan output to be saved
--stylesheet=nmap.xsl—specifies the desired XSL stylesheet
XML Output in Iceweasel
Full Path Command (Doesn’t Work)
nmap -O -sV --reason --open -oX scan.nmap.xml --stylesheet=/usr/share/nmap/nmap.xsl 10.208.42.0/24
-oX—initiates XML Output mode
scan.nmap.txt—specifies the file for the scan output to be saved
--stylesheet=/usr/share/nmap/nmap.xsl—specifies the desired XSL stylesheet
XSL From Online Source (Doesn’t Work)
nmap -O -sV --reason --open -oX scan.nmap.xml --stylesheet=http://nmap.org/data/nmap.xsl 10.208.42.0/24
-oX—initiates XML Output mode
scan.nmap.txt—specifies the file for the scan output to be saved
--stylesheet=http://nmap.org/data/nmap.xsl—specifies the desired XSL stylesheet online
Creating Portable HTML Reports
XML output option has one drawback. It cannot be utilised on workstations with a different path to the XSL stylesheet or a workstation where the XSL stylesheet doesn’t exist, as it is required every time the XML file is executed. However, there is an option to convert XML files into HTML files permanently. There are few pieces of software that can be utilised for the conversion, however I personally find xsltproc the easiest to use, and it’s included in Kali by default!
The Command Utilised
xsltproc scan.nmap.xml -o scan.html
scan.nmap.xml—defines the location and the name of XML file that needs to be converted
-o—defines direct output into a given file
scan.html—defines the location and the name of HTML file
June 3, 2014 at 12:19 pm
Awesome!! Brilliant guide.
June 3, 2014 at 12:19 pm
Reblogged this on University of South Wales: Information Security and Privacy and commented:
Awesome Guide for Nmap Output 🙂
February 4, 2019 at 10:10 am
Can someone help with how to convert xml into csv file with all the script vulnerability details